[CVE-2020-8962] D-LINK DIR-842 Stack-based Buffer-overflow
Overview
- Author: Chi Tran
- Vendor & Product: D-Link
- Version: DIR-842_REVC_RELEASE_NOTES_v3.13B09_HOTFIX
- CVE Reference: CVE-2020-8962
Vulnerability Detail
On December 31, 2019, D-Link released DIR-842_REVC_RELEASE_NOTES_v3.13B09_HOTFIX to fix the hard-coded credential issue (CVE-2019-18852).
By analyzing the firmware using QEMU, I observed that requests to /MTFWU are configured to be handled by /usr/sbin/mtfwu in HTTPD service configuration.
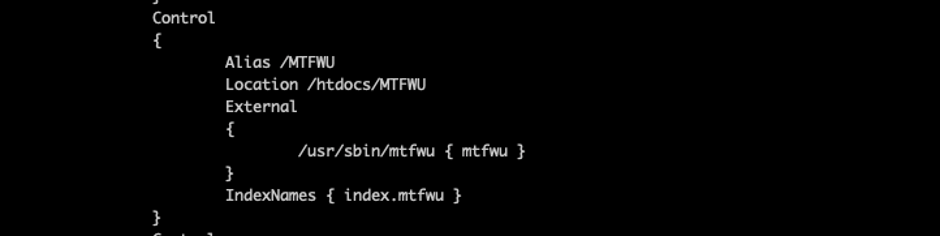
Digging into this path, the execution is symlinked by /htdocs/cgibin
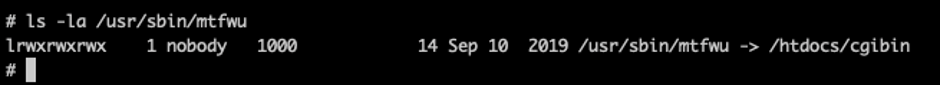
At this point, I saw the attack surface is around HTTPD service at /MTFWU endpoint. From reversing the firmware (.bin), I was able to determine the stack buffer overflow via LOGINPASSWORD parameter.
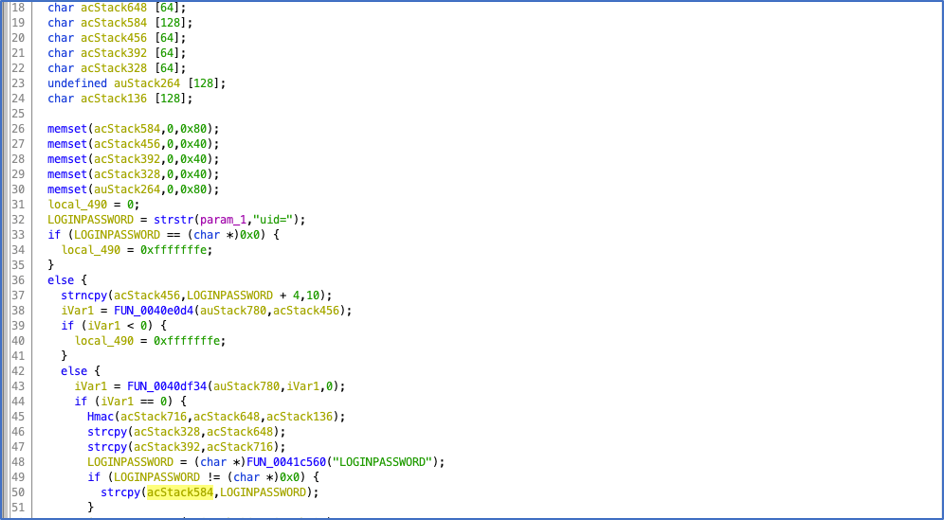
Line 19 and 50 indicate where Buffer Overflow occurs when we craft a POST request to /MTFWU with long enough value in LOGINPASSWORD parameters. This would make the service to crash and lead to an RCE as a result.
And it is always good to see these types of emails. Exploit was confirmed and bug got fixed!
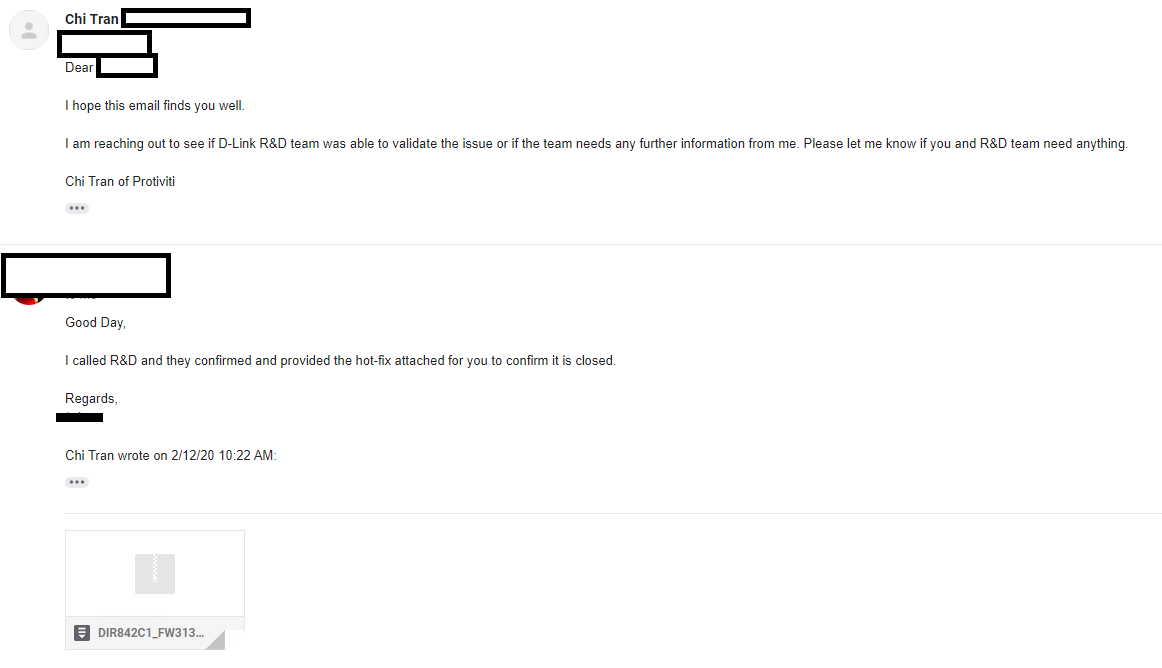
Impact
When a memory buffer overflow occurs and data is written outside the buffer, the running program may become unstable, crash or return corrupt information. The overwritten parts of memory may have contained other important data for the running application which is now overwritten and not available to the program anymore. Buffer overflows can even run other (malicious) programs or commands and result in arbitrary code execution
Remediation
https://support.dlink.com/ProductInfo.aspx?m=DIR-842
Report Timeline
01/14/2020: Discovered the vulnerability
01/15/2020: Responsible disclosure to D-Link [email protected]
01/29/2020: Followed up with the previous email since no response
02/03/2020: Followed up by sending a message via D-Link website
02/12/2020: D-Link R&D confirmed the issue and released a HOTFIX for this firmware
02/12/2020: CVE-2020-8962 was assigned to the issue
